In terms of computer security, a denial of service (DoS) attack is an action which deprives a person, group or company of resources or services that they would normally have available to them. It is generally done by targetting a persons computer or network connection. These attacks can make certain tasks impossible, such as checking e-mail or visiting a particular website. Denial of service attacks can also be much more serious and can disable your computers ability to communicate on its network completely.
Denial of service attacks can take the following forms:
When computers wish to connect through a TCP connection, they exchange TCP/SYN and TCP/ACK packets. The initial computer requests the connection with the TCP/SYN packet, and the responding computer or server sends back a TCP/ACK packet[1]. The TCP/ACK packet tells the initial computer that it is available for a connection and goes hand in hand with the responding system setting aside resources for the connection.
A SYN FLOOD sends a large amount (flood) of TCP/SYN packets to a server. The server will then treat these packets like an ordinary connection request[1]. However, the sender address in the flooded packets is forged to either an unsuspecting or non-existant address. This causes the server to be left with half-opened connections, as there is no real other side to the connection. These half-open connections consume resources on the server, specifically the number of connections it is allowed to make. Thus many legitamite users attempting to connect to the server will be unable as all of its connections are tied up in false half-open ones, denying them legitamite service.
A LAND Attack is a hybrid of SYN FLOODING, where the forged address of the TCP/SYN packet is the target computer or servers own address[1]. This causes the target machine to respond to itself continuously until it crashes.
ICMP flooding, or "smurf attacking" as it has become commonly known relies on improperly configured networks to be implemented. An ICMP flood will use the broadcast address of a specific network to send forged ICMP echo requests to every machine on that network[1]. These requests have a forged IP address of the target on that network. Each machine on the network will echo back to the victim, effectively tying up all of its communication resources when this action is multiplied hundred-fold.
Fraggle attacks are essentially the same as ICMP flooding, except that they use UDP echo traffic as opposed to ICMP echo traffic.
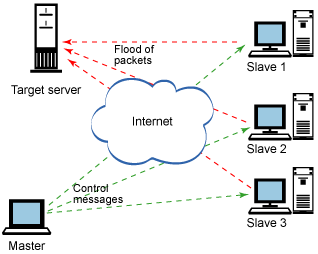
DISTRIBUTED DENIAL OF SERVICE ATTACKS
A Distributed denial of service attack occurs when multiple systems, usually at the command of a 'master' system attack a single target (or group of closely related targets). This is carried out through zombie agents spread throughout the internet. A zombie agent is a system that is compromised in such a way that it allows the 'master' system to execute a DoS attack remotely. Zombie agents are created generally through Trojan viruses, or careful exploitation on vulnerable systems by the attacker.

Zombie agents used as a whole are referred to as botnets[1], and these can be used against any ip address the master system desires. The major advantages of DDoS attacks over DoS attacks are the fact that they can generate more traffic and thus inflict more damage, they're more difficult to defend against for the victim and they can afford to be more stealthy in their actions since they rely on large numbers to succeed, making them much harder to track down.
Networks with little to no security are very vulnerable to Configuration Alteration types of attack. If an intruder is able to access the configuration files on either a router, gateway, or specific machine they can damage it severely. These attacks can vary widely in the amount of damage caused, though it is usually directly related to the amount of access an intruder can acquire. Should the intruder manage to access the routing protocols on a router, he or she can not only render its normal functions useless, but turn them into destructive flood attacks[2].
Should the intruder manage to access more sensitive information, such as registry data on a computer or server, they can disable many functions for its users.
This type of attack is chiefly the result of not restricting access to networks or machines appropriately[2]. You should always restrict physical access to the backbone and wiring of your network to prevent network disruption. Although physical destruction is the simplest form of a denial-of-service attack, it is also the most costly. Not only do you lose money for service unavailability, you also need to replace the components that have been tampered or destroyed.
Main Developer: