802.11 Wireless Security
Author: Jason Bourne
Last Revised: April 4, 2007

Wireless security covers the topics of authentication, confidentiality, and data
integrity on a wireless network. Wireless security is becoming
increasingly important as more and more wireless networks are being established. The
current state of wireless security is actually quite bad. Even 'secured'
networks are suspect to cracking.
An important fact about wireless security is that most of the current
security schemes are crackable. Using these schemes provides a false sense of
security and should be used with caution. Currently the only
scheme known to be uncrackable is WPA2.
Contents
1 Vulnerabilities of a Wireless Network
1.1 Unconfigured Networks
1.2 Malicious Association
1.3 MAC Spoofing
1.4 Wireless Hacking Software
2 Securing a Wireless Network
2.1 WEP
2.2 WPA
2.3 WPA2
3 References
4 See Also
5 External Links
Vulnerabilities of a Wireless Network
Unconfigured Networks
By far the most common form of vulnerability is simply a wireless network that has not been configured for security. In 2001 a simple drive by of the wireless networks in the area revealed that a staggering 67 percent [2] of the networks had no security at all. This means that a user could connect to the access point and start intercepting packets sent by other users on the network for malicious purposes.
Malicious Association
Malicious association is when a hacker configures his machine to act as an access point, called a ‘soft AP’, in place of an existing network [4]. What this does is allows the soft AP to respond to users requesting access to that network. Now the hacker has established a connection with a user who thinks he is connected to the existing network and may begin to send passwords or other private information unknowingly to the hacker.
Mac Spoofing
Some wireless networks secure themselves by performing authentication based on MAC addresses. MAC addresses were never intended to be used this way and are not a good form of securing a network. Tools such as Ethereal and Kismet [4] can be used to sniff out MAC addresses of an authorized user. Then the hacker can set his network card to use that MAC address, spoofing the authorized user and gaining access to the network.
Wireless Hacking Software
There is a variety of software utilities that are designed to help someone
intrude on wireless networks [2].
Airsnort: wireless network tool that passively monitors 802.11 networks and
gathers data packets to analyze to decrypt 128-bit WEP encryption. Similar
programs are WEPCrack, Aerosol, and Mognet.
Network Stumbler: a program that grabs broadcast W-Fi configuration information
and audits a network and its attached computers and users.
pong.exe: ascertains passwords, WEP encryption keys, and the actual MAC
addresses of network adapters.
Ethereal: allows a hacker to examine the live data stream from a Wi-Fi network
or capture the data stream to a disk for later viewing.
Securing a Wireless Network
WEP
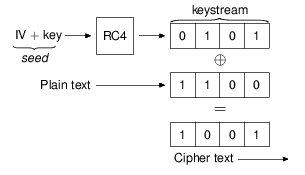
Wired Equivalent Privacy (WEP) was introduced into the 802.11 standard in 1999 [5] as a means for providing confidentiality for wireless networks. WEP is a form of cryptography that uses an RC4 key to produce cipher text given some plain text. In 64-bit WEP the RC4 key is made up of a 40-bit key which is concatenated with a 24-bit initialization vector (IV). The 64-bit key size was due to a government regulation that restricted key size. Later the restriction was lifted and a 128-bit version of WEP was released.
Vulnerbilities of WEP
WEP is not as secure as intended. It was intended that WEP could only be broken
using brute force methods, which could take days to years to break. However,
methods have been found that can break WEP in as little as 60 seconds [3]. The
hacker can simply use tools such as WEPCrack or Airsnort to perform a crack on
an encrypted network. This extreme vulnerability has made WEP obsolete.
One reason that WEP is so vulnerable is that the encryption algorithm, ICV, is
based on CRC-32. CRC-32 is intended for use in error detection, not encryption.
It turns out that it is terrible for generating a cryptographic hash [6].
The method that WEP is cracked by is a
stream cipher attack combined with a
related key attack.
The attack is based on the fact that in WEP the same key is used more than once
every 4096 packets [7].
WPA
Wi-Fi Protected Access (WPA) was introduced to replace WEP which has several known security flaws. WPA was intended as an intermediate measure while the full 802.11i standard, which includes WPA2, was being developed. WPA differs from WEP in two main ways. First, it uses a larger 48-bit IV (see WEP for the details of an IV). This increases the time between subsequent repeats of the encryption key. The second and most important difference is the Temporal Key Integrity Protocol (TKIP). TKIP dynamically changes keys frequently enough to prevent any related key attacks. TKIP requires a server for the key changes, so an alternative WPA-PSK (Pre Shared Key) was created.
Vulnerabilities of WPA
WPA is crackable [8], it just requires slightly more effort on the hacker. The process if as follows. The hacker must force a connected user to disconnect. This will cause a reauthentication of the disconnected user, at which point an encrypted version authentication password can be obtained. Now all that has to be done is a dictionary attack to recover the original password. This attack relies on a weak password selection, so to protect against it you must select a strong password.
WPA 2
WPA2 is the 802.11i standard security mechanism for wireless networks. It was introduced in June, 2004 [9] as a replacement for WEP and WPA. One main difference between WPA and WPA2 is that WPA2 utilizes the Advanced Encryption Standard (AES). AES provides a high level of encryption and authentication that prevents the known attacks on other security mechanisms.
WPA2 Vulnerabilities
WPA2 currently has no known vulnerabilities.
References
[1] http://en.wikipedia.org/wiki/Wireless_security
[2] http://www.abanet.org/lpm/lpt/articles/tch05041.html
[3]
http://www.shawnhogan.com/2006/08/how-to-crack-128-bit-wireless-networks.html
[4] http://www.governmentsecurity.org/archive/t8161.html
[5] http://en.wikipedia.org/wiki/Wired_Equivalent_Privacy
[6] http://www.networkworld.com/details/715.html
[7] http://en.wikipedia.org/wiki/Related_key_attack
[8]
http://blogs.ittoolbox.com/wireless/networks/archives/wpa-encryption-cracking-7419
[9] http://en.wikipedia.org/wiki/WPA2
See Also
Wireless Router Technology
Honeypots
Wireless Ad-hoc Network Intrusion Detection System
Advanced Encryption Method (AES)
Wardriving
External Links
Wireless Security
Wireless Security News
WiFi Wireless Home Network Security Tips
Wireless LAN Security Site