|
Honeypots
Author:
Justin Chang
A honeypot is a server or system that is intended to be used as a decoy, attracting unauthorized users for the purpose of detecting, preventing and studying their activities [1]. This type of security tool usually takes the form of a work station, file/web server or any other digital entity that may interest a malicious user [3] and appear to be part of some network which may potentially contain valuable data or resources [4]. While this tool is intended to attract dangerous users, it is actually isolated from the real network and systems – it is not an actual node accessible or used by any user or other system, nor is it integrated into the functional network of that company or organization. The decoy simply lures malicious users away from the actual systems or resources within a network, thus counteracting the illegitimate attempts to gain access to such systems (while monitoring those activities) [5]. Honeypots depend on hackers or attackers interacting with them since they are never actually meant to be used or accessed otherwise. Any interaction with such a system immediately indicates unauthorized activities [3] which can then be counteracted, monitored or stopped. Thus, honeypots are not an application nor do they provide any sort of service, instead, by being interacted with they protect the actual systems and provide vital information about attacks or activity through their inadvertent use. ContentsUses A honeypot is such a versatile tool since it has many uses in different areas of data, systems and network security. One main benefit is the ability to learn about the actions a malicious user is performing and protect against similar future attacks. Other uses include:
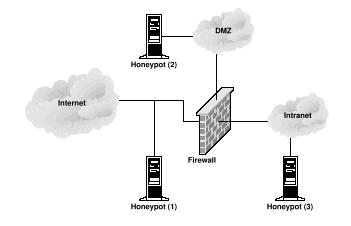
Most honeypots can be broadly categoried two ways: by their level of interaction (high or low) and type of use (production or research): High-interaction Honeypot Network (honeynet) A high-interaction honeynet is an actual network of honeypots accessible through a controlled gateway simulating all aspects of a real network [4]. This classification and type of honeypot is usually permitted to be compromised in such a way as to allow attacks from one system in that cluster to other systems in the honeynet [6]. Such actions are possible because the honeynet is not part of the real network, isolated and controlled in some manor. Low-interaction Honeypot (honeyd) Unlike a high-interaction honeynet having several honeypots, a low-interaction system pretends to be several hosts potentially providing different services. This single system fakes the different IP addresses of decoy systems instead of actually having them implemented separately like in a honeynet [4]. Production Honeypot This type of honeypot is used by companies or organizations and can be found within their networks, as they mimic some sort of node (such as a file server or workstation). A production honeypot is generally used to improve the overall security within the company or organization by protecting those resources [4]. Research Honeypot Unlike a production honeypot, a research honeypot is used by some sort of institution in order to learn more about the users who perform unauthorized activities or attacks [4]. They do not make that organization's network more secure but help other organizations learn about their attackers from the information they have gathered. ImplementationIn order for honeypots to be truly useful they must appear to be legitimate systems or resources on a network. Also, since this tool is so dynamic and versatile the design and implementation can vary drastically for each honeypot. The following section describes some of the points that should be considered during the implementation process:
Advantages:
Disadvantages:
References
McMaster University - Software Engineering 4C03 - Winter 2007 |