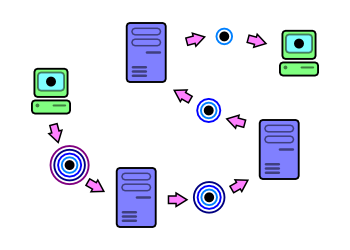
Data hops from server-to-server, with one layer of encryption "peeled" off at each hop.
Onion routing provides hosts with a method of communicating through a network, without the need to identify themselves or those they are communicating with. The ideas behind the Onion Routing project first began in 1995 with funding from the US Office of Naval Research, and a working implementation of those ideas, Tor, is currently supported by the Electronic Frontier Foundation.[1]
|
|
The project was initially funded by the Office of Naval Research in 1995. Shortly after, a prototype was implemented, targetted to the Solaris platform. By 1998, many networks implementing the first generation onion routing specification were established, although dispute over the design led towards generation 2.[1]
By that time, DARPA invested funding into the onion router project. In 2002, work on a generation 2 implementation sprouted from the code produced by Matej Pfajfar, which would be the beginnings of Tor (The Onion Router).
The Electronic Frontier Foundation supplanted the ONR and DARPA as the source of funding for Tor by the end of 2004, although the US Naval Research Laboratory continued funding for establishing hidden servers. Work on Tor still continues as the project is open under the MIT licence.
Through typical communication over a network, parties that are communicating with each other are identifiable because packet headers contain information about the source and destination of the data. An onion-routed network attempts to obfuscate this information through public key cryptography[2], and obscures it further by transmitting the data through several intermediate onion router proxies.
 |
Data hops from server-to-server, with one layer of encryption "peeled" off at each hop. |
When a service on a host wants to send data to a particular destination via onion routing, it first determines a sequence of onion routers that will provide a route for the data to travel. The path is built up one server at a time. Once this is done, the data is processed through multiple passes of encryption, one pass for each onion router that it will be travelling through. Each pass of encryption is done using each node's public key[2], with the outermost layer of encryption corresponding to the first node's public key. The encrypted data is then sent through each point in the route, decrypted once for each server.[3, 4] This is the reason for calling it onion routing: The data once encrypted consists of several "layers", making it analogous to an onion.
Because each onion router proxy decrypts one layer of encryption at a time, it cannot infer any information known by the other servers. The result is that no onion router proxy knows the full path that the data is travelling: An onion-routing proxy only knows the server the data was received from, and the server the data should be sent to. No server knows both the source and destination of the data, and only the first server knows the source, while only the last server knows the destination (these are referred to as entry and exit points or nodes in the Tor community).[3, 4]
For added privacy, new routes of communication can be rebuilt on a periodic basis. This increases the difficulty of traffic analysis by external parties. In the Tor network, circuits are reconstructed approximately once every ten minutes.[5]
Although onion routing can provide users with some degree of anonymity, it can still be susceptible to various traffic analyses and attacks. If an eavesdropper can already monitor both parties communicating with one another through an onion-routing network, neither user is guaranteed anonymity. This can be done through timing analysis.[5]
Tor is the implementation of generation 2 onion routing. The EFF continues to support it, and its development is maintained by volunteer developers. It is available on multiple platforms, including Windows, Linux, and Mac OS.
In order to use Tor effectively in anonymous communication, one must understand that onion routing is not intended to be a complete privacy tool on its own. Nothing prevents a host from transmitting data through an onion-routed network that identifies itself. Some web browsers, for instance, will relay information back to web servers about the user's configuration. This is possible through plugins such as Java and Flash, or even by submitting HTML forms.[5, 6] In this case, the safest route to take is to disable plugins, or remove them entirely, although this is not necessary with other tools such as Privoxy.
In addition, Tor (and onion routing, in general) does not concern itself with the protection of the actual transmitted data. Even though the data is encrypted with several layers during its transmission, the data is still unencrypted outside of the onion-routed network. To prevent data from being compromised in this way, one could apply TLS/SSL or some other form of encryption for further reassurance.[6]
Last revision: 06-04-2007
William Hua