Computer spyware is a form of malware commonly found on PC computers. Unlike other malware such as viruses, spyware does not usually attempt to destroy data or replicate itself en mass. Its primary function is to record information related to activity on the PC without the users consent, and send that data to an external party. This is typically used for targeted advertising, in which pop-ups appear on the users system which have been chosen based on the different types of websites visited by the user. This is also the function of another type of malware called adware. Spyware differs from malware in that spyware is placed onto the computer without the users knowledge or consent [1]. Some spyware can simply send information about the user’s computer system, while others send much more detailed information such as browsing habits, keystrokes, or even screen shots of computer activity. It is estimated there are 21 spyware infections per PC in the UK [2]. As spyware builds up on a machine, its performance begins to suffer as well, as more and more programs run in the background, hidden from the user and competing for CPU time.
Spyware is primarily used as an advertising tool. Frequently, software utilities that are free to download on the internet bundle their software with spyware as a method of generating revenue. This advertising can take the form of pop-ups on the user’s machine, alterations to the advertising contents of visited web pages, hijacking of the user’s homepage and additions of web sites to the user’s favorites list [3]. Spyware also significantly degrades system resources. This is especially true if a large amount of spyware has been installed on a user’s PC. Spyware, like all programs take up CPU time, use system memory, disk space, as well as Internet bandwidth [3]. Since user’s are usually unaware such programs exist on their machine, over time as performance continually degrades users may mistakenly believe their machines are outdated and in need of replacement. An even greater danger of spyware is its potential use for criminal activity. It is estimated that approximately 15% of all spyware is used for criminal purposes [5]. Software designed to log keystrokes, and locate sensitive documents could be used for a wide range of criminal activities including identity theft, extortion, password theft, and monitoring of instant messaging conversations [4].
Information recorded by spyware varies from program to program. Regardless of the information sent back however, a unique identifier must be sent along with the data so that the information collected from one computer can be distinguished from another. There are two common methods used to uniquely identify a PC. These are to generate a Globally Unique Identifier (GUID), or to install a cookie on the user’s machine [6]. GUID’s contain information unique to the machine’s hardware, such as serial numbers. Cookies are files that contain data which programs use. Spyware would typically create a cookie that stores computer specifications, installation version, etc. This unique information provides the key for the entry in the users database.
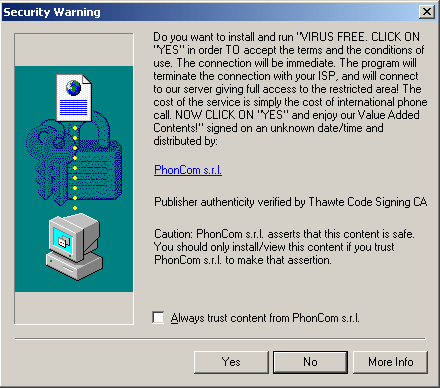
There are a number of different ways in which spyware can be installed on a PC. One of the most common methods of installation is to attach or “bundle” the software with a useful application that the user wishes to install. Often the spyware is mentioned as being part of the program in the EULA, however it is not frequently advertised as being part of the program prior to installation. Because many users do not read the entire EULA of every piece of software they install, they may unwillingly agree to having the spyware on their machines. This is a significant legal issue, as since the user technically consented to installation of the software, as legislation such as the “Spy Act” in the US makes installing an application on a computer without the user’s consent a crime, but offers no protection when the user unwittingly gives consent [7]. Another method is installation is “drive-by” downloads. This occurs when a spyware program installs itself through a security hole in a web browser. In some cases simply visiting a particular website can activate the installation, without any notice to the user [8].
One simple method of preventing spyware from entering your PC is to read the EULA of all software downloaded off the internet, or otherwise obtained free of charge. Another method is to refrain from browsing certain types of sites which are prone to containing spyware. A study done at the University of Washington found the top site categories for drive by downloading were: Games, Music, Piracy, and Adult [8]. Another method of protection is to install a spyware removal tool. These programs scan your hard drive for known spyware programs, and remove them from your system. The top rated programs from PC Security News are: Webroot Spy Sweeper, PC Tools Spyware Doctor, Computer Associates Pest Patrol, and Panicware Anti-spyware [10].
Written by Patrick McClafferty
Revised: April 5th, 2007