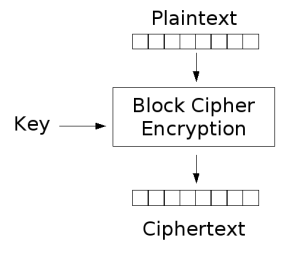
Block ciphers are a key part of encryption techniques. All block ciphers are symmetric functions that are used to encrypt plaintext data into an encrypted format. The data is encrypted in blocks of a fixed bit size and typically result in a block of cipher text of the same bit size. The encryption is accomplished using a key which is either provided by the user, or commonly created using a random number generator. This same key is used in the decryption process to obtain the original plaintext from a cipher text block. One extremely important feature of a block cipher is that it is one-to-one symmetric. That is, by applying the inverse of the encryption algorithm to a cipher text block, the original plaintext can be recovered. [1]
Generally,
Ek : P → C
E-1k : C → P
E-1k( Ek ( plaintext ) ) = plaintext [3]
The first block cipher, Lucifer, was developed in the mid 1970’s at IBM by Horst Feistel. [7]
Table of Contents |
 |
The decryption method of block ciphers is closely related to the encryption algorithm. Since all block ciphers are symmetric, applying the inverse of the encryption algorithm will always result in the original plaintext which was encrypted.
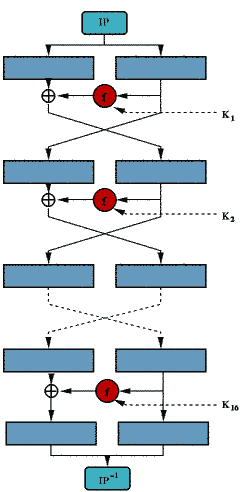 |
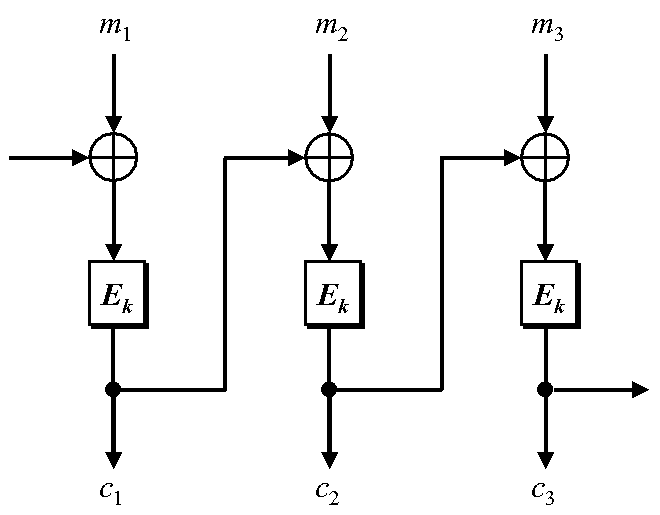
One simple way to increase the effectiveness of the encryption algorithm is to repeatedly apply the same algorithm, each iteration encrypting the message further. This is common practice in most modern block ciphers as it can be applied extremely easily once an effective encryption algorithm is found. The number of iterations, or rounds, is determined by the designer. The number of rounds selected is usually determined by the computational power available and the security level desired. It has been shown that after eight rounds, the increase in security level decreases to the point where it becomes negligible. During each subsequent round the same key can be used or a new key can be selected. [4]
 |
There exist a number of common block ciphers in use today. These are outlined in the table below.
Table 1 - Common Block Cipher Features
Name |
Year Developed |
Block Size (bits) |
Key Size (bits) |
Lucifer |
1971 |
48 |
48 |
DES |
1975 |
56 |
64 |
RC2 |
1987 |
64 |
8-128 (default 64) |
IDEA |
1991 |
64 |
128 |
BlowFish |
1993 |
64 |
32-448 (default 128) |
1998 |
128 |
128, 192 or 256 |
|
Intel Cascaded Cipher |
2006 |
128 |
128 |
[1] Connected: An Internet Encyclopedia. "Block Ciphers". April 1997. Retrieved from http://www.freesoft.org/CIE/Topics/143.htm
[2] Jenkins, Bob. “Hash Functions and Block Ciphers”. 2002. Retrieved from http://www.burtleburtle.net/bob/hash/#block
[3] Mirza, Fauzan. Royal Holloway University of London. “Block Ciphers and Cryptanalysis”. 1998.
[4] RSA Laboratories.. “What is a Block Cipher?”, Cryptography, 2007. Retrieved from http://www.rsa.com/rsalabs/node.asp?id=2163
[5] Tech Target Security Media. “What is a Block Cipher?”. SearchSecurity.com, 04 Jan 2006. Retrieved from http://searchsecurity.techtarget.com/sDefinition/0,,sid14_gci213594,00.html
[6] Wikipedia, the Free Encyclopedia. "Block Cipher". February 20, 2007. Retrieved from http://en.wikipedia.org/wiki/Block_cipher
Block Ciphers, from Connected: An Internet Encyclopedia
What is a Block Cipher?, from RSA Laboratories
Block Cipher, from Wikipedia, the Free Encyclopedia
Ian McCombe
Created for Software Engineering 4C03, Research Project
Last Update: April 04, 2007