Social Engineering
Article written by: Robert Zagorac
Last Revision: April 6, 2007.
The purpose of this article is to describe the concept of social engineering. Social
engineering is a combination, or in a more cynical sense, an
arsenal, of various methods of manipulation that one may employ to
gain access to confidential material or secrets to which they are not privy[1]. The primary characteristic of these methods is
that they are psychological in nature. This article deals with
social engineering
when used to exploit computer networks  . Social engineering often involves impersonation,
lying, conning
. Social engineering often involves impersonation,
lying, conning and dishonesty.
and dishonesty.
Social engineering is specifically effective because it bypasses intrusion detection systems  such as password
such as password  and authentication
and authentication  services, fire walls
services, fire walls  and the like, by attacking the weakest link in the chain of network security
and the like, by attacking the weakest link in the chain of network security  . This weakest link is the human element and includes everyone from network administrators
. This weakest link is the human element and includes everyone from network administrators  to users
to users  . Network security experts believe that social engineering is the easiest way to break into a
computer network[5]. Users are a
particularly weak link because:
. Network security experts believe that social engineering is the easiest way to break into a
computer network[5]. Users are a
particularly weak link because:
- They are commonly quite trusting and do not expect to be victims
- They do not question things that appear to be normal
It is important to understand that social engineering is not always an attempt to actively trick someone and that it relies on exploiting the laziness, trust, greed or lack of foresight in individuals[2].
Contents |
The Social Engineer's Tactics
The following are some of the methods and means employed by the social engineer:
Research
The first step a social engineer or group of social engineers will take towards gaining unauthorized access to an individual's workstation or organization's network will be to conduct research[1]. The social engineer is at a great advantage here because he can control the time frame. Some things a social engineer may try to discover are:
- User Information
- Names of important users (managers, administrators)
- Birth dates
- Phone numbers
- Addresses
- Periods when users are away from their workstations
- Common weak passwords
 such as users' pets' names
such as users' pets' names
Any information is valuable to the social engineer. Even something such as a persons email signature  may be useful to a social engineer as it will provide him legitimacy if he attempts to impersonate
may be useful to a social engineer as it will provide him legitimacy if he attempts to impersonate  that person through something such as email spoofing
that person through something such as email spoofing .
.
Research Methods
The social engineer has a large arsenal of research methods such as:
Asking
Due to the common trusting nature of people, including network administration and human resources department staff, it is often as simple as making a phone call to learn the names and additional personal information of employees, managers and other important people[1].
Directories and Web sites
If the social engineer is working from within the organization, employee directories are excellent places to
gather users' personal information. Also, by using networking web sites such as Face-book , it is often quite simple to locate the personal information of an individual. Trust is
exploited here because users assume that no one accessing their information has any intention to exploit it.
, it is often quite simple to locate the personal information of an individual. Trust is
exploited here because users assume that no one accessing their information has any intention to exploit it.
Dumpster Diving
User names and passwords to computer networks are often written down or printed out as hard copies. These and other sensitive security documents such as phone directories, policy manuals, memos, meeting schedules and even letterheads are eventually thrown out, only to be found during the social engineers Friday night dumpster dive[ 4] . Dumpster diving relies on the trusting nature of persons and their belief that no one would attempt to steal garbage. As well, many people are too lazy to ensure that sensitive documents are rendered unreadable prior to disposal.
Gaining Access
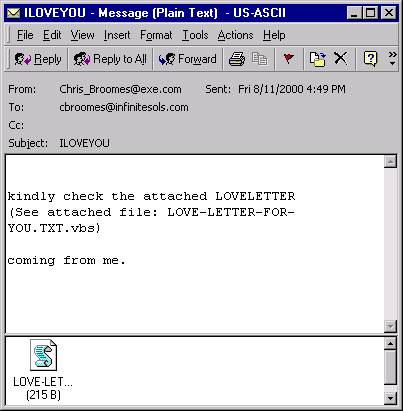 |
| The I Love You worm. A famous gimme. |
Once the social engineer has completed his research, he likely has a large amount of information that will prove invaluable in his efforts to gain access to his target.
Persuasion and Pre-texting
Pre-texting is another common method often used by social engineers, an example of which is phishing. Pre-texting
involves the social engineer setting up a fictional situation to deceive a user into performing some
action[5]. In terms of
network security, a social engineer may know a certain users account name and call technical support  requesting a password reset of that account name. He may easily impersonate the account holder
by providing personal information that he previously discovered during the research phase. Due to the large size
of many organizations, it is impossible to know everyone. This increases the likelihood of a successful pretext.
Also, the social engineer may use traditional persuasion methods such as flirtation or just plain friendliness.
Tools for identity verification such as PGP and GPG can be used to prevent
pre-texting.
requesting a password reset of that account name. He may easily impersonate the account holder
by providing personal information that he previously discovered during the research phase. Due to the large size
of many organizations, it is impossible to know everyone. This increases the likelihood of a successful pretext.
Also, the social engineer may use traditional persuasion methods such as flirtation or just plain friendliness.
Tools for identity verification such as PGP and GPG can be used to prevent
pre-texting.
Gimmes
A gimme is a form of social engineering that relies on the greed or curiosity of a user[3]. Users are often coerced into
opening email when they contain subject lines such as "You've won!" or "I Love You." even if the sender's name is
unfamiliar. As well, social engineers may create official looking emails using information discovered during the
research phase. These emails will contain attachments that install malware
that install malware or use some other trick to gain that users private information. A form of physical gimme
involves the social engineer leaving a CD or USB Key labeled "Employee Evaluation Summaries" or "Office Salary
Distribution" in a location where it is sure to be found. This will tweak the curiosity of most users who will
attempt to read the data on the CD or USB Key. Once inserted the disk runs some form of malware on the users
computer.
or use some other trick to gain that users private information. A form of physical gimme
involves the social engineer leaving a CD or USB Key labeled "Employee Evaluation Summaries" or "Office Salary
Distribution" in a location where it is sure to be found. This will tweak the curiosity of most users who will
attempt to read the data on the CD or USB Key. Once inserted the disk runs some form of malware on the users
computer.
Reverse Social Engineering
One of the most advanced methods of social engineering and also one of the most difficult to carry out is that of reverse social engineering. Reverse social engineering usually requires that the social engineer be working closely with an individual or organization. First, the social engineer sets up some sort of network problem. He then makes it known that he is the one who has the solution to that problem. Once the affected individuals are convinced of this fact, he requests certain pieces of information that he states are necessary to fix the problem such as account names and passwords, the very information he intended to gain[ 4].
Prevention Techniques
There are a number of techniques that an organization can use to ensure that users are protected from the attacks of social engineers.
Awareness
Lack of awareness is a great asset in the social engineer's favor[5]. Because so few people realize that social engineering is a serious threat, they allow themselves to be more easily victimized. Any network administrator or network service provider should be knowledgeable in social engineering methods. This knowledge could be gained through a certification such as GIAC.
Policies
An organization's security policy should include references to social engineering techniques. It should outline such things as
the types of personal information that should be kept private, how to create ironclad passwords, how to properly
dispose of sensitive documents and how to use tools such as PGP and GPG to protect sensitive
information.
should include references to social engineering techniques. It should outline such things as
the types of personal information that should be kept private, how to create ironclad passwords, how to properly
dispose of sensitive documents and how to use tools such as PGP and GPG to protect sensitive
information.
See Also
- Phishing
- Public Key Cryptography (PGP)
- GNU Privacy Guard (GPG)
- Global Information Assurance Certification (GIAC)
References
- http://www.securityfocus.com/infocus/1527
- http://www3.ca.com/securityadvisor/newsinfo/collateral.aspx?cid=53070
- http://www.answers.com/topic/social-engineering-security
- http://www.microsoft.com/technet/security/midsizebusiness/topics/complianceandpolicies/socialengineeringthreats.mspx
- http://www.computerworld.com.au/index.php/id%3B1016567243%3Bfp%3B4%3Bfpid%3B16